2015
- Toward Efficient and Privacy-Preserving Computing in Big Data Era (IEEE Network)
- A Novel Privacy-Preserving Set Aggregation Scheme for Smart Grid Communications (GlobeCom'15)
- PGuide:An Efficient and Privacy-Preserving Smartphone-Based Pre-Clinical Guidance Scheme (GlobeCom'15)
- EFPA: Efficient and Flexible Privacy-Preserving Mining of Association Rule in Cloud (ICCC'15)
- EPPD: Efficient and Privacy-Preserving Proximity Testing with Differential Privacy Techniques (ICC'16)
- TJET: Ternary Join-Exit-Tree Based Dynamic Key Management for Vehicle Platooning
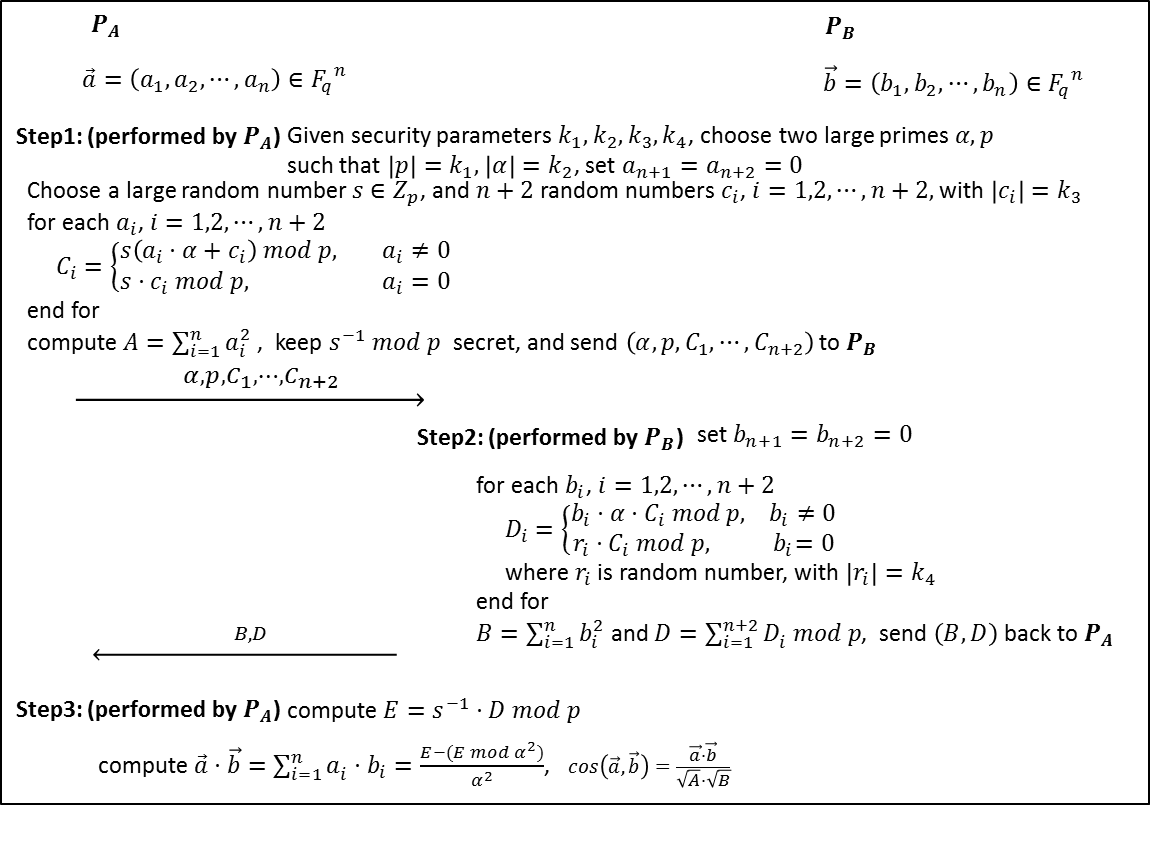
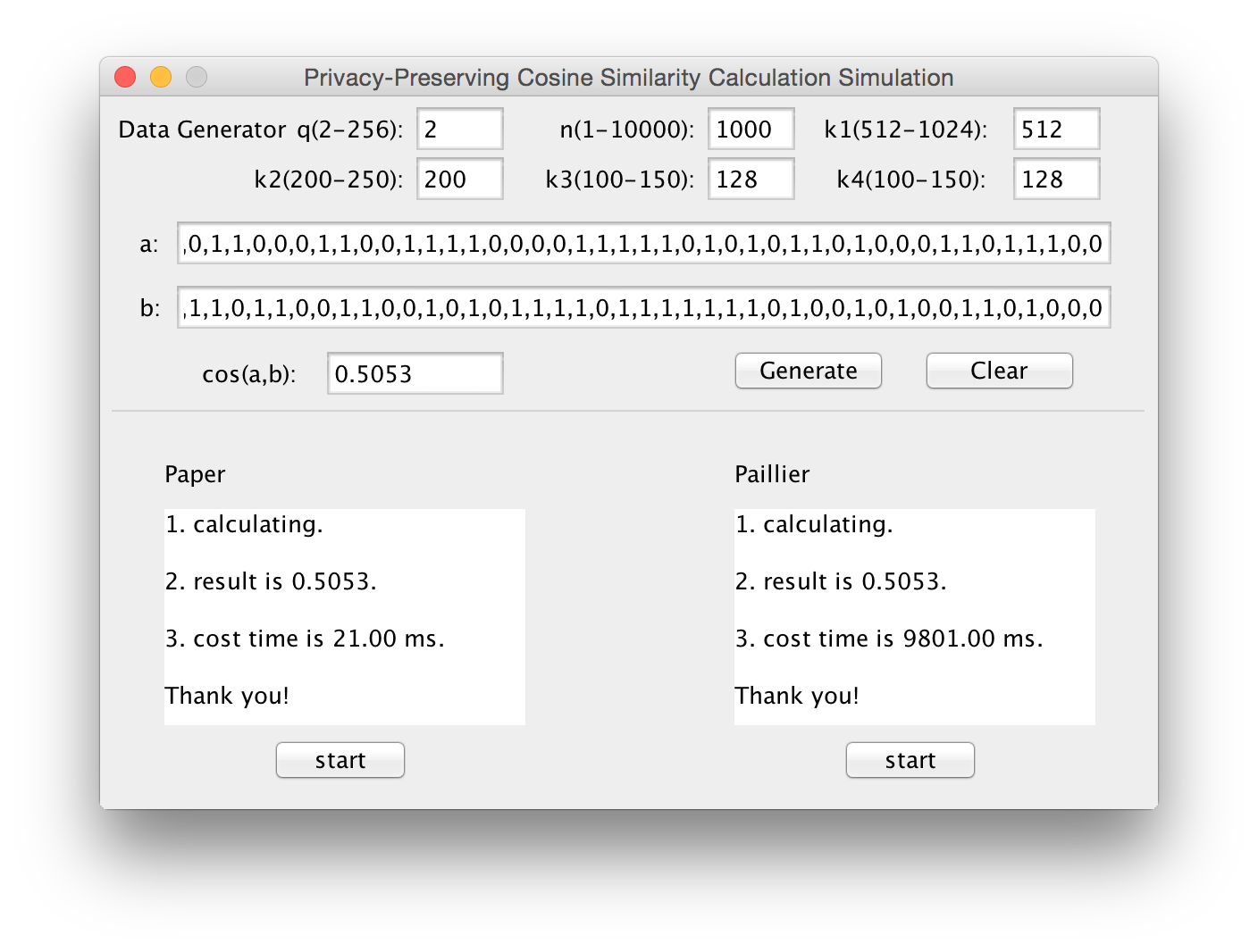
Toward Efficient and Privacy-Preserving Computing in Big Data Era
Big data, because it can mine new knowledge for economic growth and technical innovation, has recently received considerable attention, and many research efforts have been directed to big data processing due to its high volume, velocity, and variety (referred to as “3V”) challenges. However, in addition to the 3V challenges, the flourishing of big data also hinges on fully understanding and managing newly arising security and privacy challenges. If data are not authentic, new mined knowledge will be unconvincing; while if privacy is not well addressed, people may be reluctant to share their data. Because security has been investigated as a new dimension, “veracity,” in big data, in this article, we aim to exploit new challenges of big data in terms of privacy, and devote our attention toward efficient and privacy-preserving computing in the big data era. Specifically, we first formalize the general architecture of big data analytics, identify the corresponding privacy requirements, and introduce an efficient and privacy-preserving cosine similarity computing protocol (privacy preserving scalar product computation) as an example in response to data mining’s efficiency and privacy requirements in the big data era. (Rongxing Lu, H. Zhu, X. Liu, J. Liu, and J. Shao, "Towards Efficient and Privacy-Preserving Computing in Big Data Era ", IEEE Network Magazine, Vol. 28, No. 4, pp.46-50, 2014.)
Authors: Rongxing Lu, Hui Zhu, Ximeng Liu, Joseph K. Liu, and Jun Shao.
A Novel Privacy-Preserving Set Aggregation Scheme for Smart Grid Communications
In this paper, we propose a novel privacy-preserving set aggregation scheme for smart grid communications. The proposed scheme is characterized by employing a group G of composite order n = pq to achieve two-subset aggregation from a single aggregated data. With the proposed set aggregation scheme, the control center in smart grid is able to obtain more fine-grained data aggregation results for better monitoring and controlling smart grid. Detailed security analysis shows that the proposed scheme can achieve privacy-preserving with formal proof under random oracle model. In addition, extensive experiments are conducted, the results demonstrate the proposed scheme is also efficient in terms of low computational costs and communication overheads.
Authors: Rongxing Lu, Khalid AlHarbi, Xiaodong Lin, and Cheng Huang.
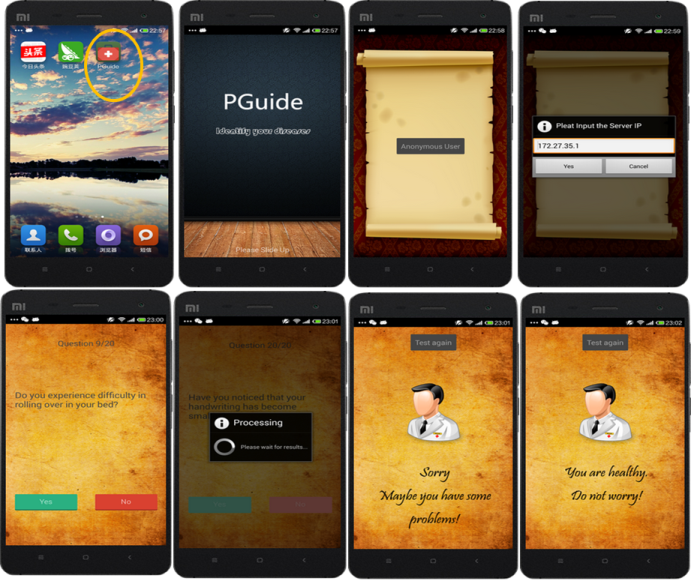
PGuide:An Efficient and Privacy-Preserving Smartphone-Based Pre-Clinical Guidance Scheme
With the pervasiveness of smartphones, mobile e-Healthcare has attracted considerable attention in recent years. Disease risk prediction, as it can assist in predicting user's disease with big data analytics techniques, has become one of important topics in the field of e-Healthcare. However, if the privacy issue is not well addressed, disease risk predication cannot step into its flourish. Aiming at addressing this challenge, in this paper, we propose a new efficient and privacy-preserving pre-clinical guidance scheme, called PGuide, which offers self-diagnosis service to medical users in a privacy-preserving way. In specific, to motivate medical users to provide more detailed health profile for accurate disease risk prediction, we introduce a privacy-preserving comparison protocol PPCP in the PGuide scheme. As a result, with enough health profile information offered by the medical users, the accuracy of disease risk prediction can be improved. Detailed security analysis shows that our proposed PGuide scheme ensures the privacy-preservation for both medical users and service provider. In addition, the performance evaluation via extensive experiments also demonstrates that our proposed PPCP protocol is much efficient in terms of low computational cost and communication overhead.
Authors: Guoming Wang, Rongxing Lu, and Cheng Huang
EFPA: Efficient and Flexible Privacy-Preserving Mining of Association Rule in Cloud
With the explosive growth of data and the advance of cloud computing, data mining technology has attracted considerable interest recently. However, the flourish of data mining technology still faces many challenges in big data era, and one of the main security issues is to prevent privacy disclosure when running data mining in cloud. In this paper, we propose an efficient and flexible protocol, called EFPA, for privacy-preserving association rule mining in cloud. With the protocol, plenty of participants can provide their data and mine the association rules in cloud together without privacy leakage. Detailed security analysis shows that the proposed EFPA protocol can achieve privacy-preserving mining of association rules in cloud. In addition, performance evaluations via extensive simulations also demonstrate the EFPA's effectiveness in term of low computational costs.
Authors: Cheng Huang, and Rongxing Lu
EPPD: Efficient and Privacy-Preserving Proximity Testing with Differential Privacy Techniques
With the ubiquity of mobile devices, location-based social networking applications have been widely used in people's daily life. However, due to the importance and sensitivity of location information, these applications may lead to serious security issues for user’s location privacy. To handle these location privacy challenges, in this paper, we propose an efficient and privacy-preserving proximity testing scheme, called EPPD, for location-based services. With EPPD, a group of users can test whether they are within a given distance with minimal privacy disclosure. In specific, EPPD is comprised of two phases: first, users periodically upload their encrypted locations to service provider; and later, users can send requests to service provider for proximity testing and obtain the final testing results. Detailed security analysis shows that EPPD can achieve privacy-preserving proximity testing. In addition, performance evaluations via extensive simulations also demonstrate the efficiency and effectiveness of EPPD in term of low computational cost and communication overhead.
Authors: Cheng Huang, Rongxing Lu, Hui Zhu, Jun Shao, Abdulrahman Alamer, and Xiaodong Lin
TJET: Ternary Join-Exit-Tree Based Dynamic Key Management for Vehicle Platooning
Vehicle platooning, which is formed by a group of vehicles traveling in close proximity to one another, nose-to-tail, at highway speeds, has received considerable attention in recent years. However, though it brings many opportunities in self-driving, the security of vehicle platooning is still challenging. In this paper, to secure vehicle platooning, particularly to secure communication and efficient key updating for vehicles in a platoon, we propose a new dynamic Ternary Join-Exit-Tree based dynamic key management scheme, called TJET, for vehicle Platooning, which is characterized by providing efficient key updating for not only vehicle joining and leaving, but also platoon merging and splitting. Specifically, we propose the notion of ternary Join-Exit-Tree, and based on the structure of ternary Join-Exit-Tree, we devise concrete algorithms for vehicle joining, vehicle exiting, platoon merging and splitting. Moreover, we also analyze the capacities and activation conditions of join tree and exit tree based on strict mathematical proofs. Detailed security analysis show that our proposed TJET holds desirable security properties including forward security, backward security and resistance to key control. In addition, performance evaluations via extensive simulations demonstrate the efficiency of TJET.
Authors: Chang Xu, Rongxing Lu, Huaxiong Wang, Liehuang Zhu, and Cheng Huang