IN THE NEWS
Have been invited to appear as an expert and provide testimony before the Canadian Parliamentary Ethics Committee — formally the House of Commons of Canada Standing Committee on Access to Information, Privacy and Ethics (ETHI) — for their ongoing study on the Protection of Privacy and Reputation on Platforms such as Pornhub...Watch the feed or Read the report
2021
Understanding Android Malware Families (UAMF) – file infector and potentially unwanted applications (Article 6)
File infector is a malware that attaches itself to APK files, which contain all the data related to an Android application. File infector gets installed with APK files, and it gets executed when the APK file is installed. The APK file can be any Android application such as a game, word processing file, ...Read PDF
File infector is a malware that attaches itself to APK files, which contain all the data related to an Android application. File infector gets installed with APK files, and it gets executed when the APK file is installed. The APK file can be any Android application such as a game, word processing file, ...Read PDF
2021
Understanding Android Malware Families (UAMF) – Adware and Backdoor (Article 5)
Mobile adware refers to the advertising material hidden inside legitimate apps infected by malware. Most of these apps are available from third-party sources. Adware continuously shows unwanted advertisements on mobile screens even if the user attempts to force-close the app...Read PDF
Mobile adware refers to the advertising material hidden inside legitimate apps infected by malware. Most of these apps are available from third-party sources. Adware continuously shows unwanted advertisements on mobile screens even if the user attempts to force-close the app...Read PDF
2021
Understanding Android Malware Families (UAMF) – Riskware – is it worth it? (Article 4)
Riskware is defined as a legitimate program that presents potential risks to the security vulnerabilities on a device. Although it is a legitimate program, bad actors use Riskware to steal information from the device and redirect users to malicious websites or perform functions at the expense of device security... Read PDF
Riskware is defined as a legitimate program that presents potential risks to the security vulnerabilities on a device. Although it is a legitimate program, bad actors use Riskware to steal information from the device and redirect users to malicious websites or perform functions at the expense of device security... Read PDF
2021
Understanding Canadian Cybersecurity Laws: refactored — our series in summary (Article 10)
In this tenth and final article in our Understanding Canadian Cybersecurity Laws series, we will look back through the previous nine articles and revisit the topics covered in each of them. Our journey begins with the first article, The Foundations, first published by IT World Canada on January 13, 2020... Read PDF
In this tenth and final article in our Understanding Canadian Cybersecurity Laws series, we will look back through the previous nine articles and revisit the topics covered in each of them. Our journey begins with the first article, The Foundations, first published by IT World Canada on January 13, 2020... Read PDF
2021
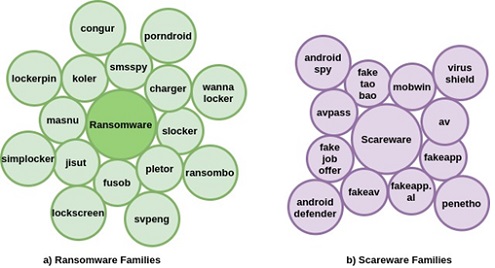
Understanding Android Malware Families (UAMF) – Ransomware and scareware (Article 3)
Ransomware is malicious software used by individuals to encrypt documents on computers or digital devices. Perpetrators demand a ransom from the owner of a device to access the victim’s documents; once in, criminals install ransomware on their mobile phone or computer... Read PDF
Ransomware is malicious software used by individuals to encrypt documents on computers or digital devices. Perpetrators demand a ransom from the owner of a device to access the victim’s documents; once in, criminals install ransomware on their mobile phone or computer... Read PDF
2021
Understanding Canadian Cybersecurity Laws: Legislative Modernization — Responding and Adapting to Technological Change in a Global Domain (Article 9)
In this article, we will discuss the Digital Charter Implementation Act, 2020, which was tabled by the government on November 17, 2020, along with its progeny: the Consumer Privacy Protection Act (CPPA) and the Personal Information and Data Tribunal Act... Read PDF
In this article, we will discuss the Digital Charter Implementation Act, 2020, which was tabled by the government on November 17, 2020, along with its progeny: the Consumer Privacy Protection Act (CPPA) and the Personal Information and Data Tribunal Act... Read PDF
2021
Understanding Android Malware Families (UAMF) – The Trojan: An impersonator in the background (Article 2)
The trojan is a sneaky impersonator that behaves like a legitimate program. It can hide in the background and steal information from the device. Trojan samples often delete, modify, block, and copy data to disrupt services provided by the operating system... Read PDF
The trojan is a sneaky impersonator that behaves like a legitimate program. It can hide in the background and steal information from the device. Trojan samples often delete, modify, block, and copy data to disrupt services provided by the operating system... Read PDF
2021
Understanding Android Malware Families (UAMF) – The Foundations (Article 1)
Android malware is one of the most serious threats on the internet and has witnessed an unprecedented upsurge in recent years. There is a need to share the fundamental understanding of behaviour... Read PDF
Android malware is one of the most serious threats on the internet and has witnessed an unprecedented upsurge in recent years. There is a need to share the fundamental understanding of behaviour... Read PDF
2021
Understanding Canadian Cybersecurity Laws: Measuring Up — Outlining Existing National Cybersecurity Legislation in Canada, the UK, Australia, and the US (Article 8)
In this article, we will outline the relevant national privacy and cybersecurity-related laws currently in effect in the United Kingdom, Australia, and the United States, as fellow common law countries... Read PDF
In this article, we will outline the relevant national privacy and cybersecurity-related laws currently in effect in the United Kingdom, Australia, and the United States, as fellow common law countries... Read PDF
2020
Understanding Canadian cybersecurity laws: Deep, dark, and undetectable – Canadian jurisdictional considerations in global encrypted networks (Article 7)
The rapid growth of encryption technology has revolutionized the online marketplace and helped to enable the creation of anonymous online networks, like the Dark Net ... Read PDF
The rapid growth of encryption technology has revolutionized the online marketplace and helped to enable the creation of anonymous online networks, like the Dark Net ... Read PDF
2020
Understanding Canadian cybersecurity laws: Peer-to-peer privacy protection - “Intrusion upon seclusion” and the protection of intimate images (Article 6)
The prevalence of digital communication has created nearly limitless possibilities for the rapid, large-scale sharing of private communications, intimate images, and personal information... Read PDF
The prevalence of digital communication has created nearly limitless possibilities for the rapid, large-scale sharing of private communications, intimate images, and personal information... Read PDF
2020

New dataset from UNB to help detect man-in-the-middle attacks
The Canadian Institute for Cybersecurity (CIC) at the University of New Brunswick has released its first-ever DNS over HTTPS (DoH) dataset funded by CIRA’s Community Investment Program. The benchmark cybersecurity dataset, named CIRA-CIC-DoHBrw-2020, ... Read PDF
The Canadian Institute for Cybersecurity (CIC) at the University of New Brunswick has released its first-ever DNS over HTTPS (DoH) dataset funded by CIRA’s Community Investment Program. The benchmark cybersecurity dataset, named CIRA-CIC-DoHBrw-2020, ... Read PDF
2020
Understanding Canadian Cybersecurity Laws: Insert Something Clever Here - Canada’s Anti-Spam Legislation (Article 5)
As we continue to adapt to the changing demands to navigate the spread of COVID-19, an increasing number of workspaces and social interactions have had to rely much more heavily on email and ... Read PDF
As we continue to adapt to the changing demands to navigate the spread of COVID-19, an increasing number of workspaces and social interactions have had to rely much more heavily on email and ... Read PDF
2020
Understanding Canadian Cybersecurity Laws: Interpersonal Privacy and Cybercrime - Criminal Code of Canada (Article 4)
The global spread of COVID-19 has been a huge catalyst in our increased reliance on digital technologies, particularly our networked communication infrastructure. With the rapid influx of demand for ... Read PDF
The global spread of COVID-19 has been a huge catalyst in our increased reliance on digital technologies, particularly our networked communication infrastructure. With the rapid influx of demand for ... Read PDF
2020
Understanding Canadian cybersecurity laws: Privacy Protection in the Modern Marketplace-PIPEDA (Article 3)
With the global spread of COVID-19, on-line scams are circulating and malicious actors have been spreading malware intended to steal individual information through both personal and corporate networks. We previously outlined... Read PDF
With the global spread of COVID-19, on-line scams are circulating and malicious actors have been spreading malware intended to steal individual information through both personal and corporate networks. We previously outlined... Read PDF
2020
Understanding Canadian cybersecurity laws: Privacy and access to information, the Acts (Article 2)
The Privacy Act and the Access to Information Act were both implemented by the Canadian federal government in 1985 and have acted as a starting point for more recent legislation... Read PDF
The Privacy Act and the Access to Information Act were both implemented by the Canadian federal government in 1985 and have acted as a starting point for more recent legislation... Read PDF
2020
Understanding Canadian cybersecurity laws: the foundations (Article 1)
The end of 2019 marked the end of a decade that has been shaped by rapid technological development, advancing data-use research, and an increasingly hyper-connective global infrastructure... Read PDF
The end of 2019 marked the end of a decade that has been shaped by rapid technological development, advancing data-use research, and an increasingly hyper-connective global infrastructure... Read PDF
2020
My recent interview with CBC
Apple, Google not doing enough to fight app-store malware, say security experts... Read PDF
Apple, Google not doing enough to fight app-store malware, say security experts... Read PDF
2019
Cybersecurity research project releases new dataset
A new dataset to support the development of real-time cyberattack detectors has been released by the Canadian Institute for Cybersecurity (CIC) at the University of New Brunswick... Read PDF
A new dataset to support the development of real-time cyberattack detectors has been released by the Canadian Institute for Cybersecurity (CIC) at the University of New Brunswick... Read PDF
2019
UNB Researchers named among top researchers for canada 150:
The national not-for-profit organization Mitacs is saluting 150 researchers from all across Canada who it says are shaping the future of the country... Read PDF
The national not-for-profit organization Mitacs is saluting 150 researchers from all across Canada who it says are shaping the future of the country... Read PDF
2017
Protect yourself and your organization in cyberspace
Earlier this year, hackers stole nearly 15 gigabytes of company information, including payroll and bank account data, from Goldcorp Inc., one of Canada’s largest mining companies... Read PDF
Earlier this year, hackers stole nearly 15 gigabytes of company information, including payroll and bank account data, from Goldcorp Inc., one of Canada’s largest mining companies... Read PDF
2016
4 NB hotels believed hit by international hacking scheme
Hackers of suspected of credit card information from guests at four New Brunswick hotels in what the InterContinental Hotels Groups believes was a North America-wise attacks... Read PDF
Hackers of suspected of credit card information from guests at four New Brunswick hotels in what the InterContinental Hotels Groups believes was a North America-wise attacks... Read PDF
2017
Cyberbullying or Cyberstalking: motives, effects, prevention and termination
In the modern-day world, information and communication technology has made it easier for people to connect with each other, resulting in both positive and negative effects for society... Read PDF
In the modern-day world, information and communication technology has made it easier for people to connect with each other, resulting in both positive and negative effects for society... Read PDF
2016

SECU-11, The security Gold medal winner of APICTA 2012, Brunai
The project entitled "A new Graphical Password For Mobile/Tablet Applications" from the University Technology of Malaysia (UTM) ... Read PDF
The project entitled "A new Graphical Password For Mobile/Tablet Applications" from the University Technology of Malaysia (UTM) ... Read PDF
2012

"GUI based on steganography" won the Gold medal on security at APICTA 2012
The Asia Pacific ICT Awards (APICTA) is an international awards program which aims to increase ICT awareness in the community and assist in bridging the digital divide ... Read PDF
The Asia Pacific ICT Awards (APICTA) is an international awards program which aims to increase ICT awareness in the community and assist in bridging the digital divide ... Read PDF
2012

Iranian computer specialist Arash Habibi Lashkari has been awarded at the 2012
Iranian computer specialist Arash Habibi Lashkari has been awarded at the 2012 national contest of MSC Malaysia Asia Pacific ICT Awards (MSC Malaysia APICTA)... Read PDF
Iranian computer specialist Arash Habibi Lashkari has been awarded at the 2012 national contest of MSC Malaysia Asia Pacific ICT Awards (MSC Malaysia APICTA)... Read PDF
2012